Anti-Spam Techniques For Email Protection

There are various anti-spam techniques for email protection. One way of filtering emails is by using the Header and language filters. Another is the X-Spam or Blacklist spam filtering technique. It is essential to use the correct anti-spam protection to ensure that you do not receive junk mail. Content filters determine whether an email is […]
Create a Secure Environment for Remote Workers

Having remote workers in your business is a great way to expand cost-effectiveness and helps your business grow. But, unfortunately, many businesses have issued remote workers limited access to the network to protect important information. Knowing this, hackers are finding creative ways to access networks and steal vital information. It is important to ensure your […]
What Is Cloud Computing?

Cloud Computing is a type of computing that offers consumers the ability to use a provider’s applications. These applications are accessible through a web browser or program interface. The consumer does not need to maintain the cloud infrastructure, though they may manage limited settings related to user-specific applications. This makes Cloud computing a flexible, cost-effective, […]
Google Unveils New Products at Pixel Event 2022
During a press event in New York City, Google unveiled the new Pixel 7 and Pixel 7 Pro devices, the brand-new Pixel Watch, and a teaser for a forthcoming 2023 Pixel Tablet. Although the devices are similar to those from last year, there seemed to be some welcomed improvements, like additional camera functions, a better […]
Microsoft Edge Improves Performance

Engineers at Microsoft recently announced performance improvements for their Edge browser. A blog post that the company published recently explained how. A blog post from the company explained how: “Beginning with Microsoft Edge 102 on Windows, Microsoft Edge automatically compresses disk caches on devices that meet eligibility checks, to ensure the compression will be beneficial […]
CISA Issues Warning Over Microsoft Exchange Server Vulnerabilities

Microsoft has warned that hackers are already using zero-day Exchange Server exploits to break into victims’ networks and steal data and that more attacks are likely to come. Microsoft has given more details about how the vulnerabilities have already been exploited, starting with attacks in August. In a small number of targeted attacks, the CVE-2022-41040 […]
Product Releases from Amazon’s Hardware 2022 Event

A number of exciting products were announced at Amazon’s Hardware 2022 event. These announcements include two brand-new Eero home networking products and the news that the next-generation Echo Dot devices will feature Eero capabilities. The first product is the Eero PoE 6 access point. Due to PoE (Power over Ethernet) technology’s popularity among enterprises and […]
What Is CIO Consulting?
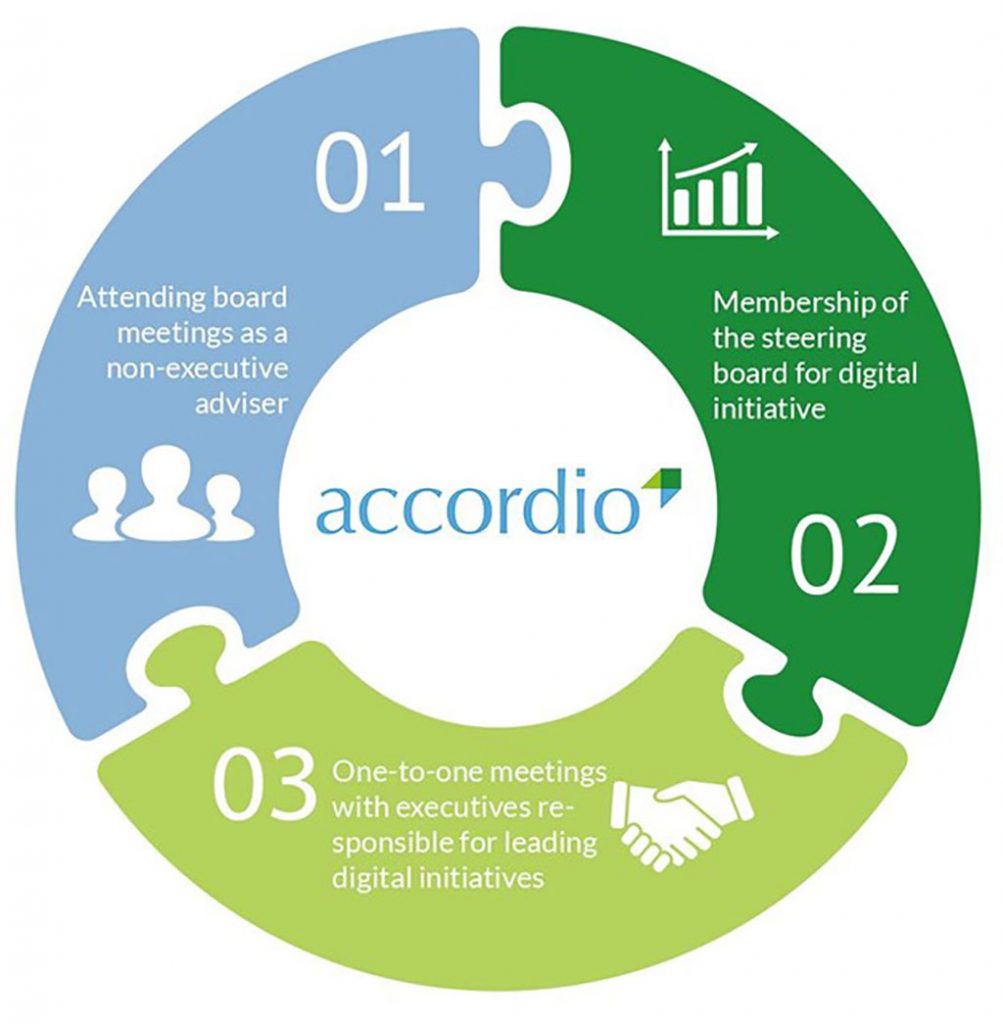
CIO Consulting is the process of planning and executing IT programs to improve business performance. It coordinates with various business units to deliver world-class services and solutions. Business process mapping is a key component of CIO consulting. It outlines the different IT activities that are required to develop a business development strategy. CIO consulting helps […]
Malware-as-a-Service Gaining Popularity

Malware as a Service (MaaS) has gained popularity over the past few years as a method of spreading malware. Typically, MaaS is provided at a monthly, annual, or lifetime subscription price. Once a threat actor obtains access to the malware, they can target individuals through various tactics. A relatively new MaaS has emerged, called Erbium. […]
Tesla Introduces Optimus Robot Prototype
Tesla introduces the humanoid Optimus robot prototype and claims to be aiming for a price of under $20,000. After the event started, Tesla’s eagerly anticipated humanoid robot was unveiled. The prototype walked unfettered across the stage. Tesla’s CEO, Elon Musk, stated that the team is working to make the robot accessible as soon as possible […]
