- For Enquiry
- 847-868-9253
- 847-868-9208
The Danger Of Holiday Phishing Scams: How To Recognize And Avoid Them To Stay Safe This Holiday Season
October 22, 2023
Mastering Passwords: Essential Practices for Digital Security
November 17, 2023Written by Matias Keib

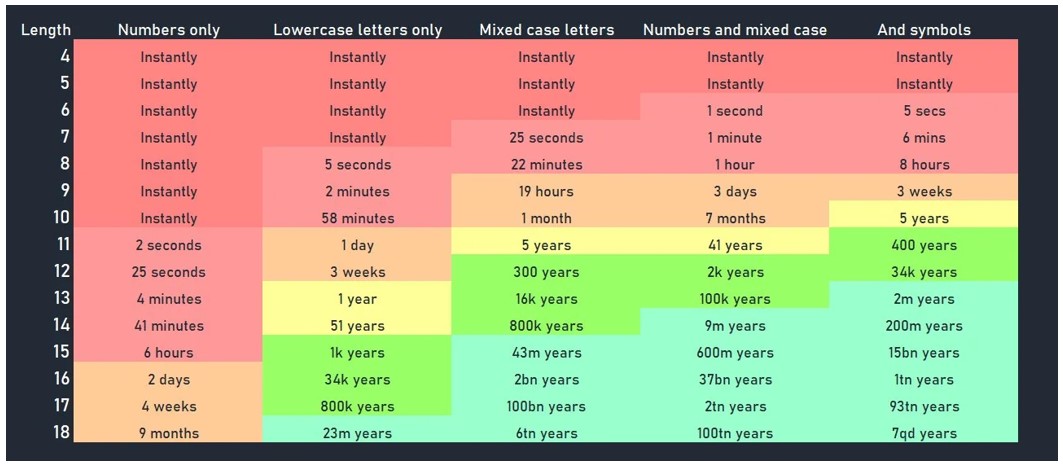
Nowadays, there is not a single service or tool you access through the internet that will not require sign in credentials (username and password), and if by any chance you happen to find one, please stay away from it. As passwords became easier to crack over time, applications and services started to demand stronger ones to protect their users. There’s even a very interesting password strength chart that displays how much time it would take an attacker to brute force it, depending on its length and character utilization. I am leaving an example in the capture below:
Nonetheless, no matter how strong your password is, it will end up being cracked sooner or later. In this article, you will learn why MFA is so important, what it can do for you (professionally as well as personally) and best practices towards its utilization.
Phishing: The Path of Least Resistance
Hackers, or let’s call them digital con artists, don’t just rely on brute force; they play a cunning game of deception. They know that the human element is often the weakest link in security, and they exploit it through phishing. This is not about casting a wide net with obvious lures; it’s a sophisticated psychological play.
Imagine receiving an email that perfectly imitates the familiar branding of your bank, complete with logos and legal disclaimers. It addresses you by name, perhaps even references recent transactions, and then nudges you to act — maybe a password reset or an account update. It feels routine, but this is the phishing hook, baited with social engineering tactics designed to bypass your rational guardrails. It preys on trust, urgency, and fear.
Phishing can also masquerade as a desperate plea from a colleague, a fraudulent charge alert, or even a message from your boss asking for quick action. The goal is the same: to coax you into handing over your credentials voluntarily. It’s the digital equivalent of a thief masquerading as a bank inspector to gain access to the vault. By the time the real bank realizes the deception, the thief is long gone, and your data is on the auction block in the deep web’s shadiest markets.
The success of phishing attacks lies in their psychological finesse, which makes even the most robust password defenses irrelevant. Why break down the door when you can get the keys handed to you with a smile? It’s not that everyone is prone to falling for such tricks. A seasoned systems administrator or a security-savvy professional would likely spot the ruse. But attackers don’t pick battles with the well-armored; they look for the easiest entry, and that’s often through an unsuspecting end user.
This is where you come into the picture. You may think your single end user account isn’t much of a trophy. But it’s not about the single account; it’s about the door it unlocks. Your account is a gateway to potentially thousands of contacts, sensitive corporate data, and privileged access that could be exploited to widen an attack’s reach dramatically.
The Consequences
Every boardroom discussion around cybersecurity seems to echo with a familiar refrain: “Let’s focus on growth, not gates and guards.” This is the common chorus, where investing in operations and business expansion wins over fortifying firewalls. But consider this: what’s the point of scaling your business if you leave the back door wide open for anyone to waltz in and plunder?
Let’s paint a picture that’s closer to home for you. You’ve poured resources into R&D, marketing, maybe even a state-of-the-art CRM system. Now, imagine the fallout if that intellectual goldmine were to leak. Your groundbreaking product plans, your meticulously crafted marketing strategies, all paraded on your competitor’s table. Worse still, your employees’ and customers’ personal information becomes a commodity in the murky waters of the dark web. The lawsuits, the loss of trust — it’s a domino effect that could topple even the mightiest of corporate reputations. And reputation, unlike a subscription or a software license, isn’t something you can just click and buy back.
Yes, cybersecurity tools and frameworks do demand investment, and the financial commitment tends to scale with the size of the enterprise. My stance has always been clear: proactive measures like Security Information and Event Management (SIEM) or Extended Detection and Response (XDR) are crucial. Yet, when it comes to bang for your buck, MFA stands out. It’s not just about the affordability or the ease of implementation; it’s about fortifying your defenses in a world where cyber threats are constantly evolving.
By integrating MFA, you’re not just patching a vulnerability; you’re transforming your security posture from reactive to proactive. Think of MFA as the sentry who never sleeps, the guardian that stands vigilant when human error, the eternal wildcard in the cybersecurity deck, plays its hand.
MFA: The first line of defense against attackers
Comes MFA, the showstopper for attackers. But what is it?
At its core, Multi-Factor Authentication (MFA) is an enhanced security measure that requires more than one piece of evidence to authenticate a user. Unlike static passwords, MFA adds dynamic layers of verification that significantly reduce the risk of unauthorized access.
After entering your user credentials (which include your username and password), the service you’re trying to access—be it your email, SharePoint, a web application, or virtually anything on the internet—will prompt you for a second form of authentication. This is where the various MFA methods come into play:
- SMS-based Verification: A straightforward method where the service sends a 6-digit code to your mobile phone via SMS, which you must enter to proceed.
- Voice Call Verification: Instead of a text, you receive a phone call, and an automated voice reads out the code required for access.
- Authenticator Apps: These apps, such as Google Authenticator or Microsoft Authenticator, generate time-sensitive codes that change every 30-60 seconds, adding a formidable obstacle for would-be attackers.
- Push Notifications: A push notification is sent to your phone through an authentication app. You simply press ‘Approve’ on the notification to authenticate, streamlining the process.
- Smartphone Biometrics: Many MFA systems integrate with your phone’s biometric sensors, requiring a fingerprint or facial recognition scan to verify your identity.
- FIDO Keys: For those looking for even greater security, FIDO keys offer a physical token that must be present during login. They may connect to your phone or device via USB, NFC, or Bluetooth, and often require a simple touch to activate.
The beauty of these codes, especially those generated by authenticator apps, is their ephemeral nature—they change every minute or so, making it exceedingly difficult for attackers to use them even if they are somehow intercepted.
What’s critical to understand is that MFA’s strength lies in its layers. By requiring something you know (like a password) and something you have (like your phone or a FIDO key), it creates a dual factor shield that secures your digital presence effectively.
For instance, let’s say an attacker has discovered your password. Without MFA, they’re one step away from accessing your account. But with MFA enabled, they hit a significant hurdle—they would need your phone to receive the SMS, your physical presence for the biometric scan, or your FIDO key to proceed. This extra step is simple for you but complex for cybercriminals to bypass, thereby protecting your data with a robust layer of defense.
The Unsafe Validation Methods
In the arsenal of cybersecurity, not all weapons are created equal. While MFA stands as a formidable barrier, certain methods have vulnerabilities that can turn them from shields into potential liabilities. Let’s scrutinize the less secure forms of MFA that users like you should be cautious about:
- SMS and Voice Call Validation: These methods may seem convenient, but they share a common weakness: SIM swap attacks. This is not a threat confined to any one region—it’s a global issue. In a SIM swap scam, your phone number is hijacked, redirecting all your messages and calls to a device under the attacker’s control. So, while you’re left wondering why your codes never arrive, someone else is breezing through your digital life with them.
- Push Notifications: At first glance, they’re a modern solution—no codes, just a simple tap. But beneath the surface lies a vulnerability to what’s known as ‘MFA Fatigue Attacks.’ Here, attackers bombard you with authentication requests. Amidst this digital onslaught, fatigue sets in, or a distracted tap in a rush, and just like that, you’ve inadvertently granted an intruder access to your most precious asset: your data.
These methods, while part of the MFA family, carry risks that can be exploited, turning your defense mechanism into an attacker’s tool. It’s the digital equivalent of having a state-of-the-art lock… that sometimes opens with the wrong key.
The Best Validation Methods
For those of us deeply entrenched in the world of cybersecurity, selecting the right MFA method is akin to choosing the highest-grade armor for battle. We meticulously evaluate all potential vulnerabilities before endorsing a solution. Because in the realm of digital security, the right tool, improperly implemented, can be as risky as having no tool at all. Therefore, when it comes to MFA, we champion methods that minimize risk and maximize security for you, the user.
Authenticator Apps: These digital sentinels offer a robust form of verification. They live on your device and generate a fresh 6-digit code every 30 seconds, which you enter during the login process. It’s a moving target that’s incredibly difficult for attackers to hit. For an even more seamless experience, apps like Microsoft Authenticator offer a challenge-response option. A login attempt will prompt a two-digit code on your screen, which you’ll match in the app, creating a transparent and virtually impenetrable verification process.
FIDO Keys: Imagine a physical key for your digital doors. FIDO keys are exactly that—dedicated devices designed for security-first authentication. Whether they’re prefabricated or custom-made, these keys don’t just lock your account; they secure it with a complexity that’s nigh impossible for attackers to replicate. Typically favored by those in sensitive roles, FIDO keys are becoming increasingly user-friendly for anyone prioritizing their cyber safety.
Lastly, while not a standalone validation method, smartphone biometrics adds an additional layer of security. They ensure that even if your phone is unlocked, the gateway to your MFA codes remains sealed behind your unique biometric signature. For instance, the Microsoft Authenticator app will request the same authentication method you use for unlocking your phone to open the app itself. So, if your phone falls into the wrong hands and your screen is locked, your MFA credentials remain secure. Remember, as a good practice, always lock your phone—and your laptop—whenever you step away.
Conclusion
In today’s digital age, MFA stands as a critical defense, not merely for safeguarding organizational assets but for protecting our individual online identities. While organizations may hesitate to implement MFA, fearing it might inconvenience users, this slight adjustment pales in comparison to the robust protection it offers. Employees and end-users should be educated on the value MFA adds, not just within their professional sphere but across their entire digital footprint. By embedding security into the user experience, MFA becomes less of a hurdle and more of a seamless step in the digital routine, one that users will appreciate for its safeguarding benefits.
The reality of cybersecurity today is that the cost of proactive defense through measures like MFA is far less than the price of recovery from a security breach. Companies must weigh the minimal investment in MFA against the exorbitant costs associated with data loss, legal liabilities, and the erosion of trust. In this light, adopting MFA is a strategic move that aligns with both fiscal prudence and a commitment to a secure, resilient future. By championing MFA, organizations not only protect themselves but also contribute to the broader effort of creating a safer digital ecosystem for all.