Written by: Matias Keib
In a recent article, I highlighted a stark reality: even the strongest passwords are vulnerable to being cracked.  This vulnerability can arise from various attacks, such as brute force, phishing, or simply poor security practices. I also discussed how Multi-Factor Authentication (MFA), when paired with secure validation methods, can mitigate the risks posed by compromised passwords. But does this mean passwords become redundant in the presence of MFA? Not exactly.
This vulnerability can arise from various attacks, such as brute force, phishing, or simply poor security practices. I also discussed how Multi-Factor Authentication (MFA), when paired with secure validation methods, can mitigate the risks posed by compromised passwords. But does this mean passwords become redundant in the presence of MFA? Not exactly.
Before you can even implement MFA on any service or application, a password is essential. Moreover, maintaining a strong password is crucial to minimize ‘noise’ – those unnecessary alerts that can overwhelm system administrators. Imagine this scenario: your password is weak and frequently guessed by attackers. While your MFA is effectively blocking these unauthorized access attempts, it also triggers alerts each time your compromised credentials are used. This situation not only burdens your system admins with constant false alarms but also signifies a lingering security risk.
Advanced users often rely on passwords for robust encryption and secure offline storage of critical files. Take, for instance, the creation of a PGP (Pretty Good Privacy) Key pair, used for encrypting files or sending secure emails. In this scenario, your private key – a crucial component of data security – is shielded solely by a password. There’s no MFA to back you up here, underscoring the need for a formidable password. In this article, I’ll guide you through the essentials of crafting a unique and strong password and provide a set of best practices to enhance your IT security. So, let’s jump right in and step up your password game!
Password Puzzles: Easing the Headache for Sysadmins and Users Alike
As a sysadmin, I’ve seen it all: the eyerolls, the sighs, the frustration. Yes, I’m talking about the dreaded password policy. For end users, regularly updating passwords and remembering complex combinations can feel like a Herculean task. But it doesn’t have to be a battle between security and convenience. In this article, I’ll share some practical tips to make password management a breeze for everyone, balancing security with ease of use.
If you’re not a tech wizard, you might be all too familiar with the password predicament at work. But here’s the thing: it’s not just about following company rules. It’s about safeguarding your digital life – at work and beyond. Think of it as upgrading your home’s security. You wouldn’t settle for a flimsy lock on your front door, so why do the same with your online information? Stick with me, and I’ll show you how to strengthen your digital defenses with simple yet effective password practices.
Whether you’re a seasoned sysadmin or someone who finds tech talk a bit daunting, there’s one thing we all have in common: the need for secure passwords. In the next section, I’ll break down the key dos and don’ts of password security. From crafting a password that’s tough to crack to avoiding common pitfalls that can leave your accounts vulnerable, I’ll cover the essentials that apply to everyone, regardless of your tech understanding level.
Dos:
- Long Passwords: Aim for at least 12 characters. The longer, the better! Here’s a chart you can rely on.
- Complexity is Key: Use a mix of uppercase and lowercase letters, numbers, and symbols to thwart brute force attacks.
- Passphrases: Think of a random, quirky string of words. Hard for others to guess, easy for you to remember.
- Regular Changes: Change your passwords if you suspect any security risk. And remember, variety is the spice of a secure digital life!
- Sysadmins: Implement policies in ADDS or your chosen security tool to automate this.
- End-users: Keep your personal accounts safe too by changing passwords periodically.
- Unique Passwords: One account, one unique password. It’s like having a different key for every door.
- Two-Factor Authentication (2FA): Add an extra layer of security. Learn more about 2FA [here].
- Password Managers: Your best friend for managing those complex passwords without losing your mind.
- Stay Informed: Keep up with the latest in password security. Your digital defense should evolve as threats do.
- End-users: Pay attention to your company’s IT security courses.
- Sysadmins: Stay on top of the latest training.
- Phishing Awareness: Know how to spot and avoid phishing scams. Don’t hand over your ironclad password to anyone!
- Breach Checks: Regularly use tools like “Have I Been Pwned” to see if your password’s been compromised.
- Sysadmins: Consider using XDR or EDR for automated breach detection.
Don’ts:
- Avoid the Obvious: Stay away from common words or phrases like ‘password’ or ‘123456’.
- Personal Info is a No-Go: Birthdays, pet names, or other easily found info from your social media? Not in your password.
- Keep it Secret, keep it Safe: Writing down passwords? A big no. Especially on sticky notes or unencrypted files.
- Password Sharing: It’s a solo journey. For sysadmins, use tools like RBAC or IAM for secure access management. And never share over chat or calls.
- Same Password, Big Risk: Using the same password for multiple accounts is like using one key for every lock in your life. Not safe.
- Alerts Are Your Friends: Don’t ignore them. They’re like the smoke alarm of your digital house.
- End-users: See something suspicious? Tell your IT team ASAP.
- Sysadmins: Act fast on confirmed compromises.
- Beware of Links: If it looks fishy, it probably is so Don’t click!. Both IT personnel and end-users, stay alert!
- Don’t ignore Password Updates: Regular changes keep your digital doors locked tight.
- No Simple Patterns: Easy patterns are easy for hackers. Keep it complex, even on your mobile PIN.
Password Managers: Your Digital Key Ring
Throughout this article, I’ve frequently mentioned the use of password managers. Why? Because they’re a game-changer in managing your digital security. Think of them as a digital key ring – keeping all your unique keys (passwords) in one secure, easily accessible place.
Offline vs. Online Solutions
When it comes to choosing a password manager, you have two main types: offline and online. I personally lean towards offline solutions – think of it as keeping all your keys in a safe at home. They’re more secure since you have complete control over your data. However, online (cloud-based) solutions are also viable, offering convenience and the added security of Multi-Factor Authentication (MFA) for accessing your password vault.
Understanding the Basics
Let’s demystify how password managers work. Their three core functions are:
- Creating Strong Passwords: They generate complex passwords for you, making each account tough for hackers to crack.
- Secure Storage: Think of it as a digital safe. If used correctly, it’s nearly impenetrable, keeping your passwords locked away from prying eyes.
- Organizing Passwords: No more squinting at your screen trying to find the right password. Password managers categorize and store them neatly, so you find what you need without the hassle.
Creating passwords
Creating the perfect password can sometimes feel like a tightrope walk between complexity and memorability. If you’ve ever tried typing a highly complex password and got it wrong a few times, you’re not alone. I’ve been there, and I know the struggle is real, especially for those who aren’t tech enthusiasts. The challenge is to make a password that’s hard to guess, long enough, and a mix of different types of characters – not an easy feat to achieve.
This is where password managers come to the rescue. They have a fantastic feature that takes the pain out of this process: an automatic password generator. With this tool, you can create passwords that are as complex and unique as needed – and the best part? You don’t have to memorize them.
Let me show you how it works with KeePass, one of my go-to password managers. In the following screenshot/capture/description, you’ll see KeePass’s password creation tool in action. It effortlessly combines length, complexity, and randomness to give you a password that’s virtually uncrackable, yet you won’t need to burden your brain trying to remember it.
The following capture displays the password creation tool of KeePass, one of my favorite password managers:
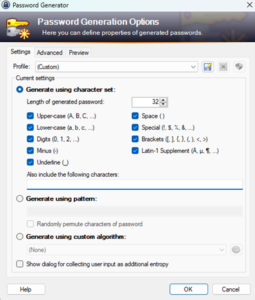
In KeePass’s password creation tool, you have the flexibility to tailor your password to your security needs. You can choose the length, which is a key factor in password strength – generally, the longer, the better. The tool also allows you to mix various character types, such as uppercase, lowercase, numbers, and symbols. An interesting feature is the ability to include characters from different languages, adding an extra layer of complexity to your password.
Moreover, KeePass provides several methods for generating a password. Each method has its unique approach, offering varying levels of security and complexity. I plan to explore these methods in more detail in an upcoming post. This will give you a better understanding of how to maximize your password security using the features available in KeePass. Keep an eye out for that if you’re interested in deepening your knowledge about effective password management.
Storing them securely
After creating your strong password, the next step is to store it securely, and the password manager is an ideal place for this. However, securing your password manager is just as crucial. You’ll need a robust master password for access, whether it’s an offline or online manager. The master password should strike a balance between being memorable and secure. You don’t want it to be so complex that you risk losing access to all your stored passwords. On the flip side, a too-simple password or one written on a post-it note defeats the purpose of security. A viable alternative is using a key file, which eliminates the need to remember a password while maintaining security. I’ll delve into setting this up in an upcoming tutorial on password managers.
Organizing Passwords in Categories
Managing numerous passwords without proper organization can be as frustrating as sifting through a pile of unsorted documents. Thankfully, password managers offer organizational features like folders. For instance, you can group all your finance-related passwords in one folder and work-related ones in another. This not only tidies up your digital space but also speeds up the process of finding a specific password when needed, thanks to the integrated search tool. Efficient organization within your password manager can save you time and reduce the hassle of password retrieval.
Conclusion: Empowering Your Digital Security
Throughout this article, we’ve explored the critical importance of passwords and the strategies to make them robust. From crafting strong passwords to utilizing a password manager, these tools and techniques are designed to simplify compliance with complex security policies – a relief not just for tech enthusiasts but for anyone who’s ever felt overwhelmed by the demands of digital security.
By incorporating these practices into your routine, you’re not only fortifying your organization’s defenses but also significantly boosting your personal digital security. This makes unauthorized access to your accounts much more challenging for potential intruders.
The use of a password manager transforms the task of managing passwords from a daunting chore into a manageable, even effortless, activity. With features like one-click password copying and secure storage, the hassle of remembering and organizing complex passwords becomes a thing of the past. This shift not only makes your digital life more secure but also more streamlined and stress-free. So, as we conclude, remember that each step you take towards better password practices is a step towards a more secure digital presence.