- For Enquiry
- 847-868-9253
- 847-868-9208

Minimizing IT Downtime: A Survival Guide For Law Firms
May 10, 2024
Coolest Consumer Products at CES 2024
May 21, 2024Did you know that a staggering 81% of data breaches are due to weak or stolen passwords? And over 50% of people use the same passwords for both personal and work accounts, leaving their organizations vulnerable. The harsh reality is that hackers attack every 39 seconds, on average 2,244 times a day. The good news is that implementing multi-factor authentication can block over 99.9% of account compromise attacks. However, with 64% of Americans having experienced a major data breach, it’s clear that stronger authentication measures are needed.
Enter the Consumer Authentication Security Maturity Model (CASMM), created by renowned cybersecurity expert Daniel Miessler. CASMM is a framework that helps organizations assess and improve their authentication security practices, ensuring they stay ahead of the ever-evolving cyber threats.
In this blog, we’ll dive into the world of CASMM, exploring its different levels and what they mean. By the end, you’ll have a solid understanding of security posture using this powerful model.
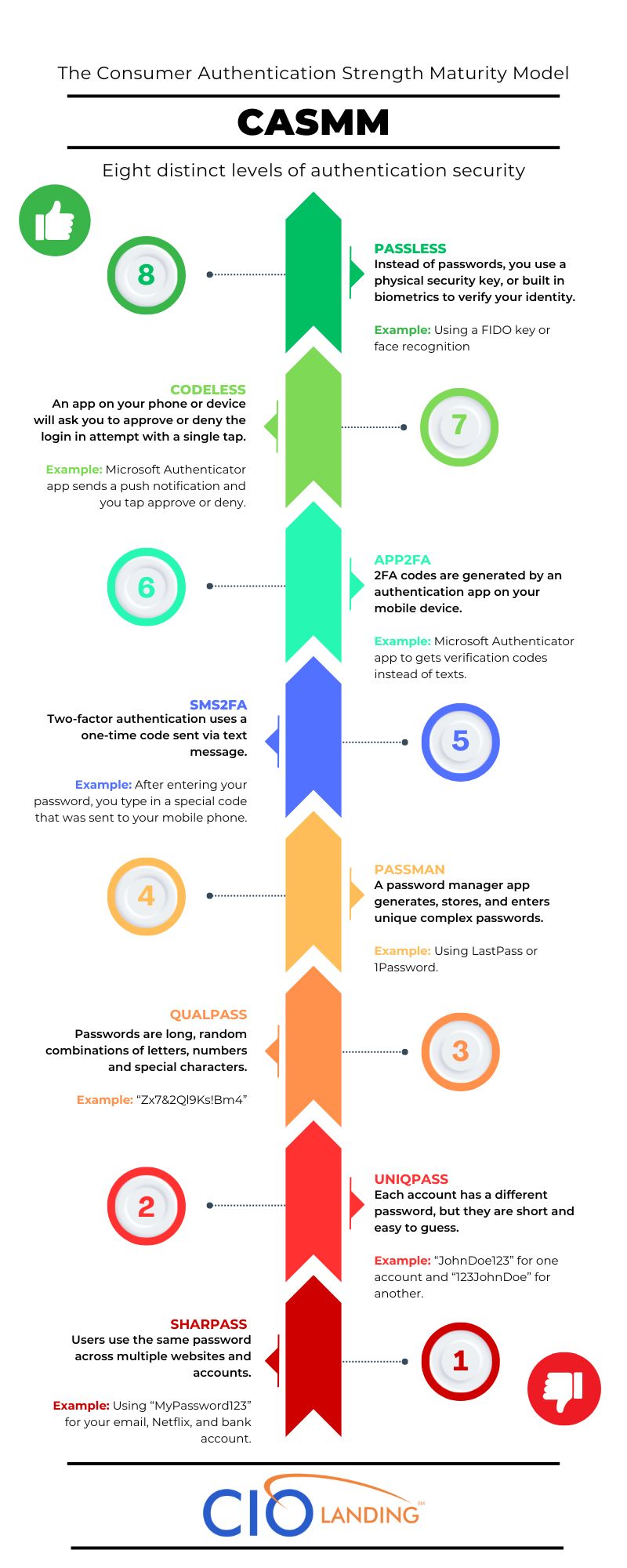
The Eight Levels of CASMM
The CASMM outlines eight distinct levels of authentication security. Each level represents a step up in protection from the previous one. Let’s explore each level in detail, including its description, potential vulnerabilities, and real-world examples to illustrate how they work.
Level 1: Shared Passwords (SHARPASS)
Description: Users use the same password across multiple websites and accounts.
Risk: Highly vulnerable to credential stuffing attacks. This is when hackers use leaked password lists to try and gain access to other accounts by reusing those same passwords.
Example: Using “MyPassword123” for your email, Netflix, and bank accounts.
Level 2: Unique Passwords (UNIQPASS)
Description: Each account has a different password, but they are often short and easy to guess.
Risk: Susceptible to live password guessing, where hackers try common words, patterns, and combinations to crack the passwords.
Example: “JohnDoe123” for one account and “123JohnDoe” for another.
Level 3: Quality Passwords (QUALPASS)
Description: Passwords are long, random combinations of letters, numbers, and special characters.
Risk: Still at risk if the passwords are leaked in data breaches and subjected to cracking attempts by hackers.
Example: “Zx7&2Ql9Ks!Bm4”
Level 4: Password Manager (PASSMAN)
Description: A password manager application generates, stores, and enters unique, complex passwords for each account.
Risk: Vulnerable if the password manager itself is hacked or the master password is stolen.
Example: Using 1Password or LastPass.
Level 5: SMS-based 2FA Codes (SMS2FA)
Description: Two-factor authentication (2FA) uses a one-time code sent to your mobile phone via text message to verify it’s really you trying to log in.
Risk: These text message codes can be intercepted by hackers through phishing tricks to steal your mobile number, or by convincing your phone carrier to transfer your number to a new SIM card they control (called SIM swapping).
Example: After entering your password, you’re asked to type in a special code that was sent to your phone to complete the login process.
Level 6: App-based 2FA Codes (APP2FA)
Description: 2FA codes are generated by an authentication app on your smartphone or mobile device.
Risk: Bad actors could try to trick you into revealing the codes through phishing scams, or if your device gets a virus or malware, it could allow hackers to secretly access the codes.
Example: Using the Microsoft Authenticator app to get verification codes to enter during login instead of texts.
Level 7: App-based Codeless 2FA (CODELESS)
Description: Instead of entering a code during login, an app on your phone or device will ask you to approve or deny the login attempt with a simple tap.
Risks: Malware on your device could potentially approve login requests without your knowledge. Hackers may also try to trick you into approving a login you didn’t intend to through social engineering tactics. Additionally, if your device is lost or stolen, an attacker could attempt to forcibly approve requests.
Example: The Microsoft Authenticator app sends a push notification asking “Is this you trying to log in?” and you tap “Approve” or “Deny”.
Level 8: Passwordless (PASSLESS)
Description: Instead of passwords, you use a physical security key or your device’s built-in biometrics (fingerprint, face ID, etc.) to verify your identity.
Risks: Physical security keys can be lost, damaged or stolen. Biometric data could also potentially be faked or hacked, though this is extremely difficult.
Example: Using a FIDO security key that you insert into a USB port, or using your smartphone’s fingerprint scanner to log in instead of a password.
The Future of Authentication Security
Emerging Trends
The world of authentication security is rapidly evolving, with new trends and technologies emerging that could shape the future of CASMM. One area gaining significant traction is biometrics – using unique biological characteristics like fingerprints, facial recognition, or even behavioral biometrics like keystroke patterns to verify identity. As biometric systems become more accurate and affordable, they offer a convenient and secure passwordless authentication option.
Another exciting development is the use of artificial intelligence (AI) and machine learning for risk-based authentication. Instead of static rules, AI can analyze a user’s typical behavior patterns and log-in attributes in real time to determine risk levels and adapt authentication requirements accordingly. This intelligent contextual analysis could allow seamless access for low-risk scenarios while enforcing stricter MFA for anomalous login attempts.
As these and other innovative authentication methods mature, we may see CASMM expand to incorporate new higher levels of security. The core principles of strong, multi-factor authentication will remain, but the tactics will continue advancing.
Staying Ahead of Threats
No matter how sophisticated authentication technologies become, one immutable truth remains – cyber threats will also continue evolving in complexity and deviousness. Attackers will persistently seek new vectors to compromise credentials and identities.
Organizations must stay proactive and commit to continuously evaluating their authentication posture against the latest threats. At CIO Landing, we ensure your security measures don’t stagnate. We help you navigate the CASMM levels, and continuously apply the latest best practices to keep your systems secure. Our approach maintains ease of use while providing robust protection, helping your business stay ahead of emerging cyber threats.
Make cybersecurity education and awareness an ongoing initiative for your staff. Emphasize the importance of understanding the risks and practicing good security hygiene, especially given the vulnerabilities associated with lower levels of the CASMM. Regular training helps employees recognize and respond to threats, reducing the risk of cyber threats.
It’s equally critical to have an Incident Response Plan (IRP) in place. An IRP ensures your organization can quickly and effectively respond to security incidents, minimizing damage and downtime. By prioritizing continuous education, and awareness, and having a robust IRP, you ensure your team is well-equipped to protect your organization and swiftly handle any security incident that may occur.
The future of authentication security will be a continual arms race. But by adopting a defense-in-depth approach guided by CASMM, you can ensure your organization remains a formidable and resilient target.
Conclusion
In today’s ever-evolving cybersecurity landscape, robust authentication practices are indispensable for protecting your business, your data, and your customers. Throughout this blog, we explored the Consumer Authentication Security Maturity Model (CASMM) – a powerful framework for assessing and strengthening your organization’s authentication security posture.
We discussed the eight distinct levels of CASMM, ranging from the highly vulnerable shared password approach up to cutting-edge password-less biometric and security key methods. Each level represents an incremental step toward better protecting your digital assets and mitigating the risks posed by cyber threats. Staying proactive through continuous improvement, ongoing training, and diligent threat monitoring will be critical for maintaining a strong security posture.
In the digital age, authentication is the lynchpin of cybersecurity. By understanding the principles of CASMM, your organization can implement robust multi-factor authentication, drastically reducing your exposure and building trust with your employees and customers. Protect what matters most by making authentication a core priority.
About the Author: Juan Carlos Bosacoma
Juan Carlos Bosacoma, the CEO of CIO Landing, is a seasoned expert in cybersecurity and IT management. With decades of experience in the industry, Juan has dedicated his career to helping businesses protect their digital assets and improve their IT infrastructures. He is the author of the insightful book “Sitting Duck: Why Your Business is a Cybercriminal’s Ideal Target,” where he shares his extensive knowledge of cybersecurity threats and best practices for safeguarding organizations.